The background of the coinbase May 2025 breech
The US’s largest cryptocurrency exchange received an unwanted email from an unknown threat on 11 May 2025 by the Coinbase. He claimed to have sensitive information about his customers and demanded a ransom of $ 20 million.
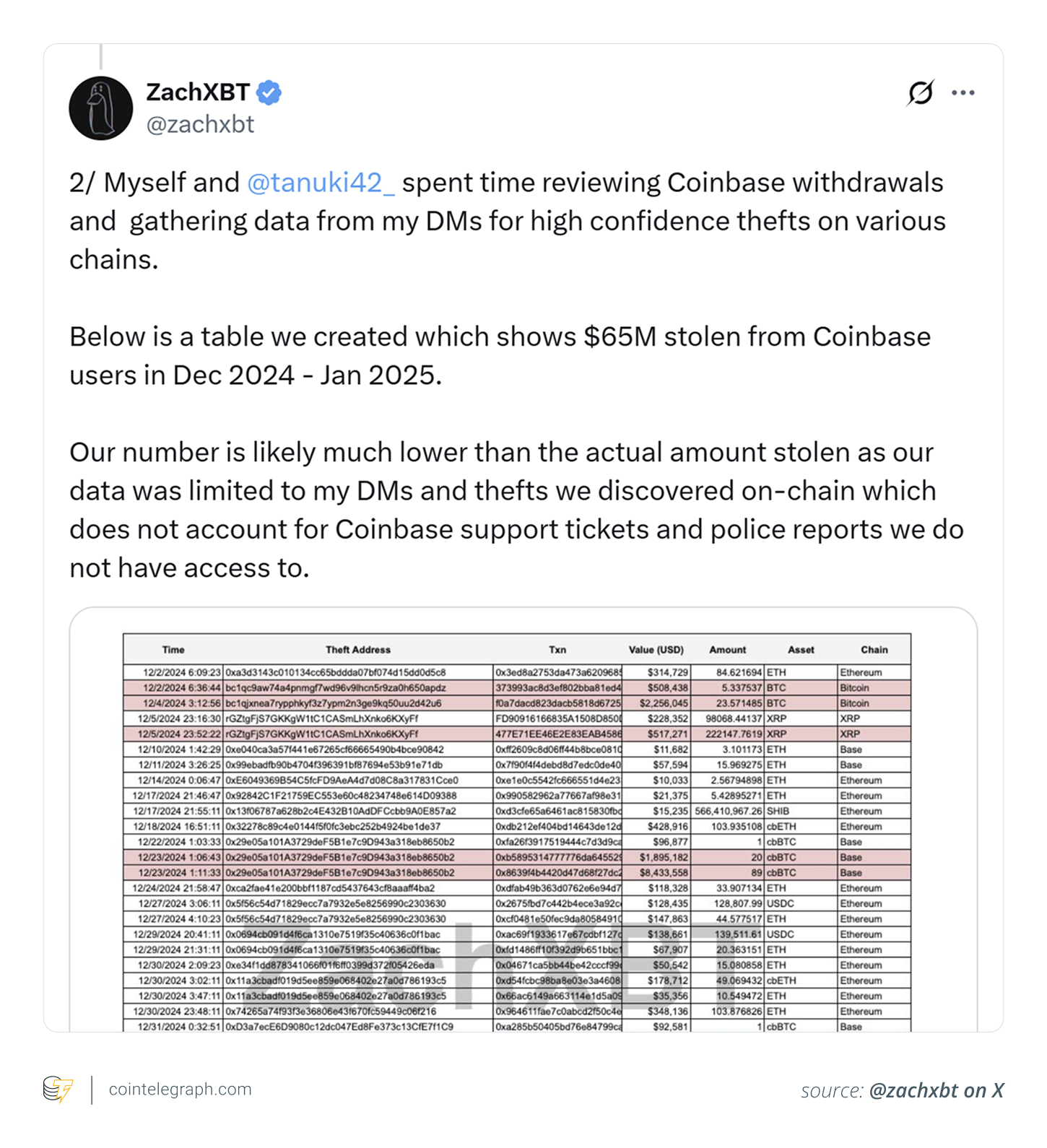
Before investigating the violation, it is interesting to understand how it happened in a public company that spends millions monthly Cyber securityIn February, blockchain investigator zachxbt Informed Increase the theft of coinbase users. He blamed the aggressive risk model and indicated the failure of the coinbase to stop $ 300 million in annual loss Social engineering scam,
A table Zachxbt shared on X stole a $ 65 million from users between December 2024 and January 2025. He also said that the actual loss could be more, as his data came only by his direct messages about onchain theft, and the coinbase support tickets and police reports were excluded.
The fear of a cyber criminal stealing valuable information was corrected on May 11 when the Coinbase published a blog post, confirming that during the data breech, the account, ID images, phone numbers, home addresses and partially hidden bank details were stolen.
On May 21, the same danger actor Repressed About $ 42.5 million from bitcoin (BTC) Ether (ET) Through thorchain. they used Ethereum The transaction input data to write “El Bojo”, following it with a meme video of NBA player James, makes fun of a cigar to smoke, jokes at ZachuxBT, who later flagged off the message on his Telegram channel.

What happened: Coinbase Breach’s Timeline
2025 coinbase breech was not one Specific crypto hack Including smart contracts or blockchain weaknesses. Instead, it was like a traditional IT safety failure, which was marked by internal formulas manipulation, corporate espionage and an attempt to recover a forced recovery.
Below is the breakdown of how the incident came to light:
- Insider recruitment and information theft started: To steal information from the coinbase, unknown cyber attackers started recruiting some foreign customer service agents (located in India) working for the coinbase. These internal sources were paid to leak sensitive customer data and internal documentation, especially around customer service and account management systems. The stolen information was for the future copying scams targeting users.
- Security detection and employee expires: The internal security team of the coinbase eventually detected suspicious activity associated with these employees. Employees involved were rapidly terminated, and the company alerted the affected users. Although only 69,461 accounts were affected, a fraction of the user base of the coinbase, the depth of the stolen personal data made the breech significant.
- Forced recovery attempt through email (May 11, 2025): Coinbase received an unwanted email, claiming internal system details and individual identifying information (PII). Later it was considered reliable in 8-K second filing.
- Coinbase refuses to pay $ 20M ransom (May 14, 2025): Instead of forcibly accepting recovery, the coinbase flipped the script. The company reported a violation of law enforcement, publicly disclosed this and gave a reward of $ 20 million for the leading information for the arrest of the attackers, converting defense into a crime.
- Violation Disclosure and Public Notification: Shortly after the SEC filing, the coinbase publicly confirmed the violation, clarifying the scope and nature of the attack. There was a data breech notification Filed With the office of the Main Attorney General, 69,461 users were officially affected.
This timeline shows how a crypto company gave different reply to an attempt to an attempt for transparency, resistance and bold counters. This can change the way you respond to dangers from cyber criminals.

Do you know North Korea’s Lazarus Group has stolen more than $ 6 billion in Crypto since 2017, including a record -breaking $ 1.46 billion in 2025.
Which data was compromised in Coinbase Data Brech in 2025?
According to a notification letter issued by the Coinbase, the attackers sought this information as they had planned to start a social engineering attack. The information they stolen can help them look reliable for the victims and possibly celebrate them to transfer their money.
The Coinbase expanded the information that the danger actors had received access and what they could not do.
What did the attackers get
- Name, address, phone and email
- Government – ID Pictures (eg, Driver License, Passport)
- Masked Social Security (Last Four Points)
- Account data
- Masked bank account number and some bank account identifier
- Corporate data (including communication for documents, training materials and support agents)
What did the attackers not get
- Login Credit or 2FA Code
- Private keys
- Access to Coinbase Prime Accounts
- Customer
- Access to any coinbase or coinbase customer hot or cold wallet
Do you know In 2022, crypto.com lost $ 30 million from 483 accounts. Initially, he claimed that no money was stolen, but later accepted the breech and back victims, exposed the importance of transparency in Crypto hack.
How Coinbase responded to 2025 criminal data violations
In response to 2025 data breech, the coinbase implemented a comprehensive strategy to reduce damage, support affected users and strengthen its safety infrastructure.
Important action taken by Coinbase:
- Refusal to give ransom: The coinbase rejected a ransom of $ 20 million sought by the attackers. Instead, the company set up a reward fund of $ 20 million for the leading information for the arrest and punishment of those responsible people.
- Customer Reimbursement: The company committed to reimburse the customers who were cheated in sending money due to violation. Estimated cost for treatment and reimbursement Category Between $ 180 million and $ 400 million.
- Stolen Protection Services: The company is providing all the affected individuals with one year of credit monitoring and identity protection services. This includes credit monitoring, $ 1 million insurance reimbursement policy, identification restoration services, and dark web monitoring, to find out if any personal information appears on illegal online platforms.
- Increased customer safety measures: The affected accounts will require additional ID verification for large withdrawal, including compulsory scam-awareness signs to prevent further social engineering attacks.
- Strong support operations: The coinbase is opening a new support hub in the US. This has implemented strong security control and monitoring to all places to prevent internal threats.
- Cooperation with law enforcement: The company is working closely with the US and International Law Enforcement agencies. The internal sources involved in the violation were abolished and referred to for criminal prosecution.
- Transparency and Communication: Once the Breach was recognized, the Coinbase immediately informed the affected customers. It is offering updates about the steps being taken to address and address it.
These measures reflected the coinbase’s commitment to customer safety and its active approach to cyber security challenges.
Do you know Crosschain bridgeLike the Nomad Bridge, the complex in 2022 caused a loss of $ 190 million Smart contract Weaknesses. These bridge hackers are preferred because they store large -scale crypto assets, making them an attractive goal.
How to stay safe in the event of data violations like coinbase
In view of the large -scale data violations of crypto platforms, you should take active steps to protect yourself from social engineering attacks.
Here’s how you can be safe in such an event:
- Share with those who share sensitive information anytime: Scammers often pose as auxiliary staff or safety agents after a violation. They can push you towards pushing money forward Crypto wallet They share with you or disclose sensitive information under various texts. Never share your password, Two-factor authentication (2fa) Code with such impersonators, or recovery phrases. No Crypto exchange You will ask the crypto to move to “new” or “safe” wallets.
- Allow the wallet address to allow: Some exchanges provide this feature, which prohibits withdrawal on the pre-controlled wallet address you fully controlled. This prevents unauthorized transfer, even if your account is compromised.
- Enable strong 2fa: For 2FA, use a hardware security key or a reliable certification app. Avoid relying on SMS-based 2FA, which is unsafe for sim-swapping attacks.
- Be cautious with unwanted communication: If someone claims to be from a crypto platform, hang immediately and asks for safety credentials or requests asset transfer. Do not respond to unknown texts or emails with your personal information.
- Lock first, check later: If anything seems suspicious, lock your account immediately through the app or platform and report the event for customer aid through official channels.
- Stay informed: Regularly review the safety tips and updates from your crypto services to avoid identifying and increasing your crypto services.



